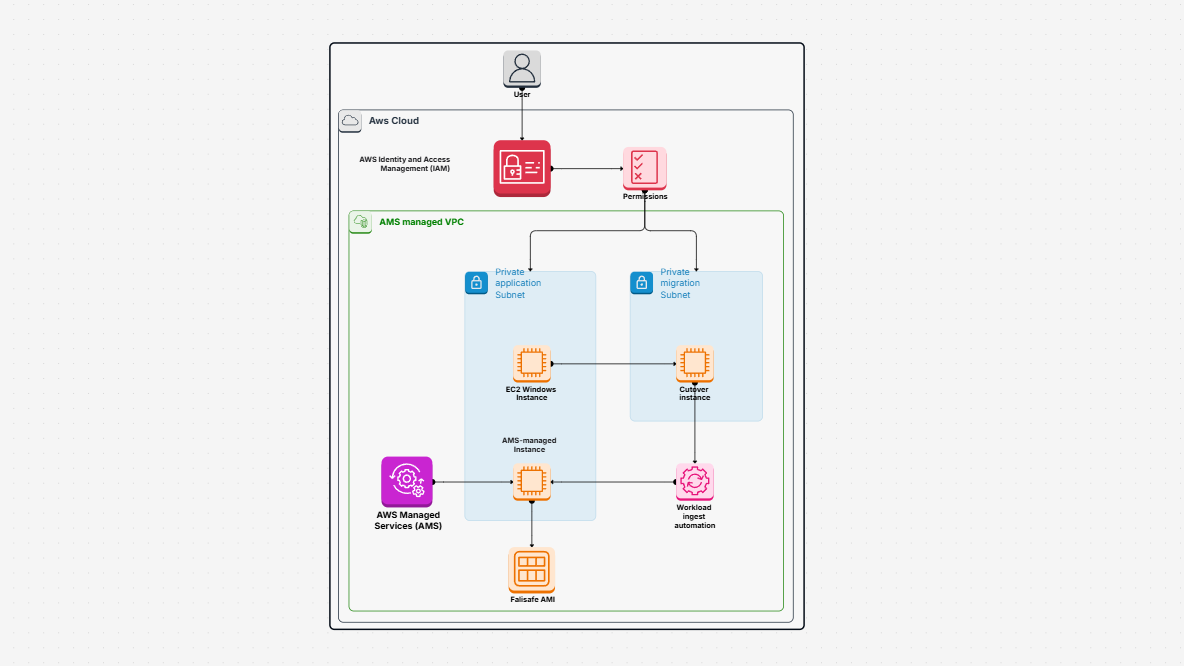
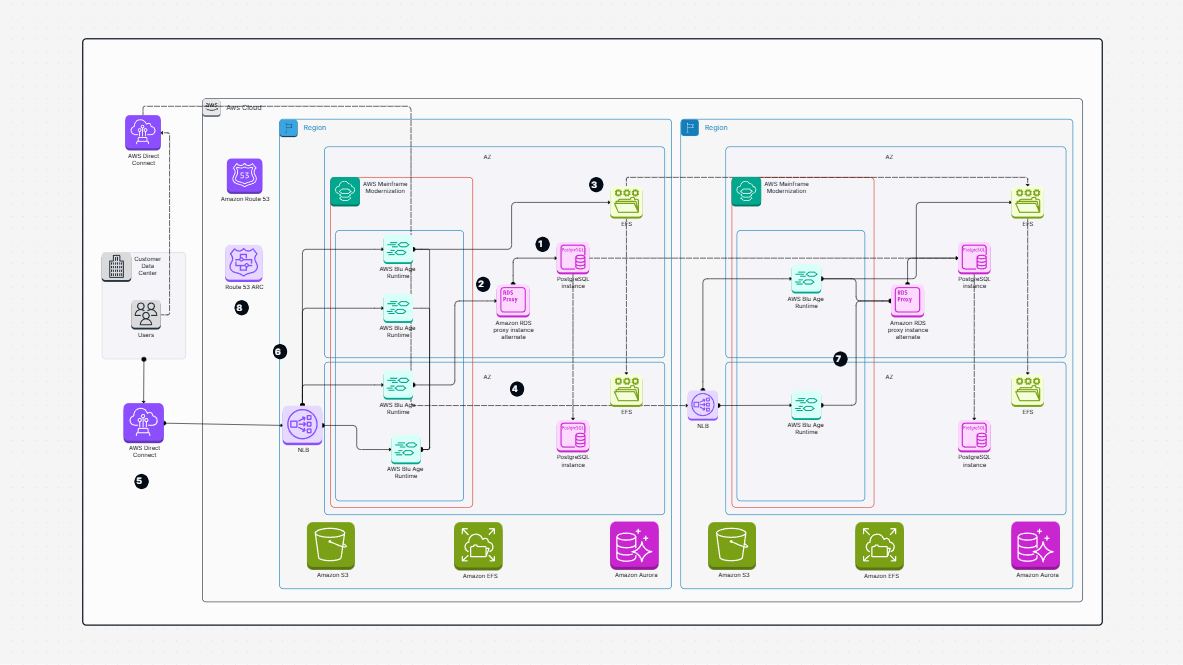
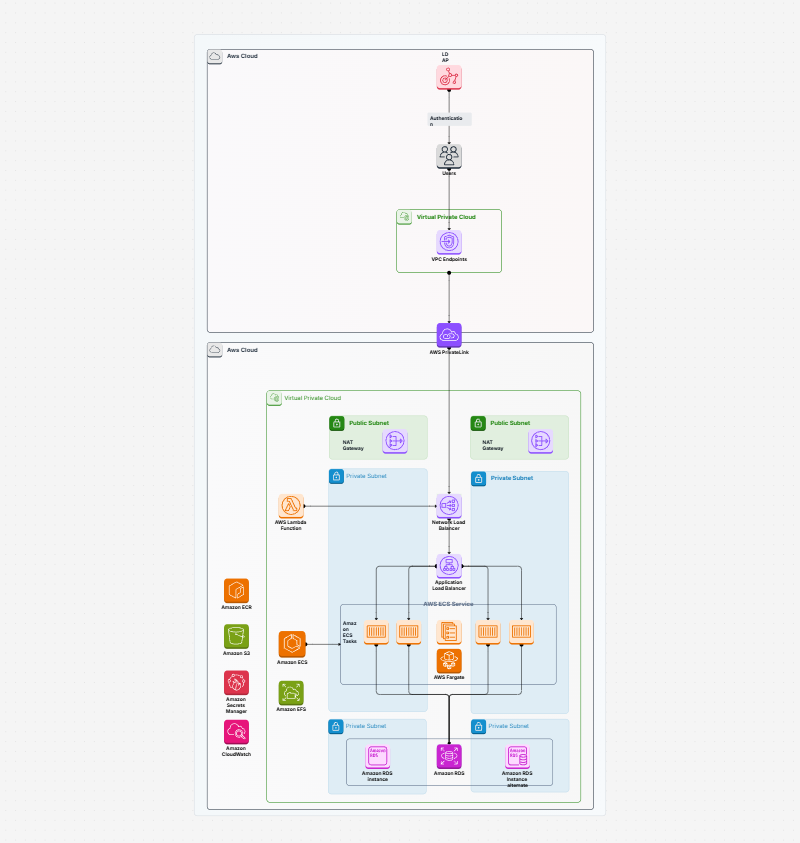
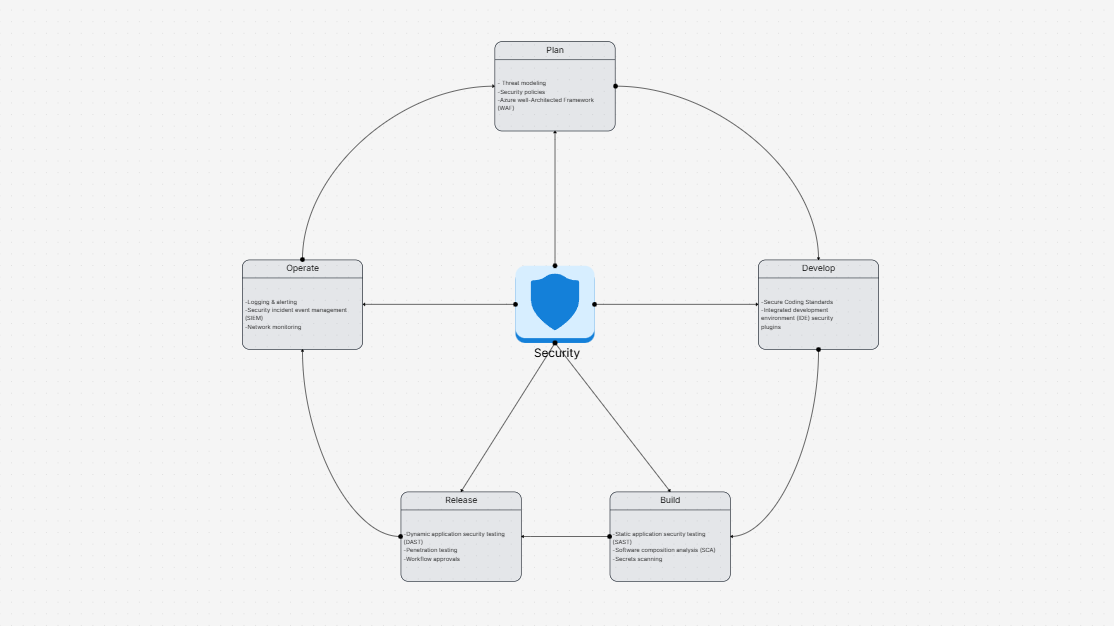
WorkHub

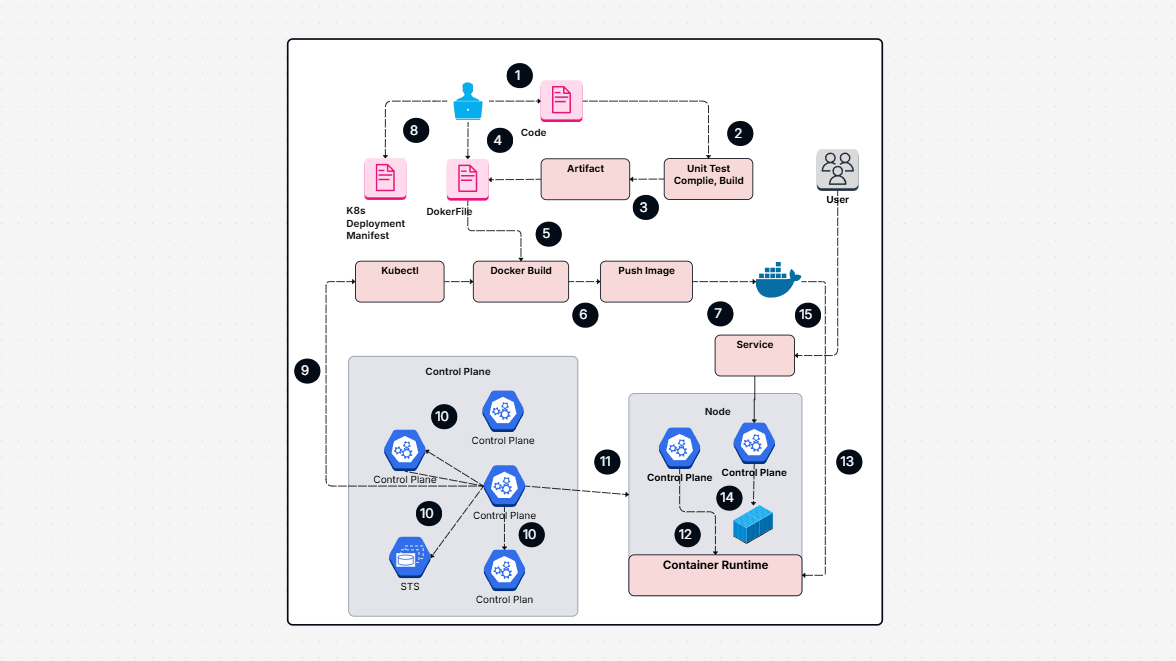
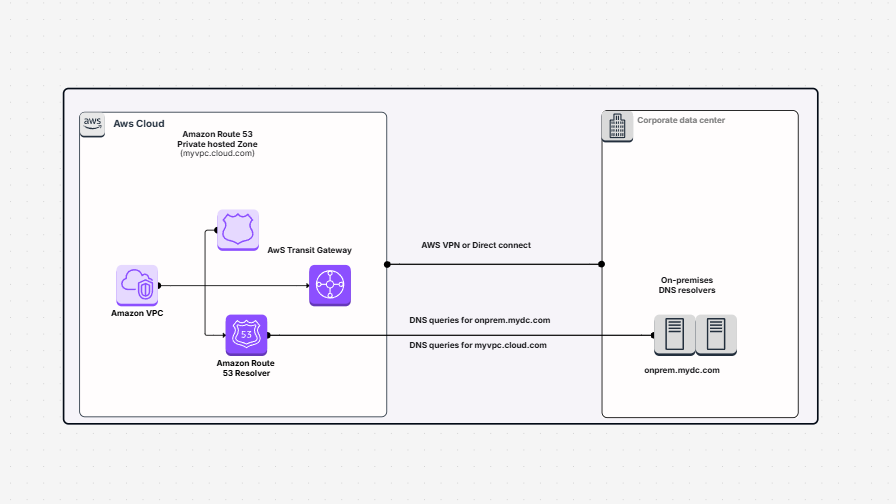
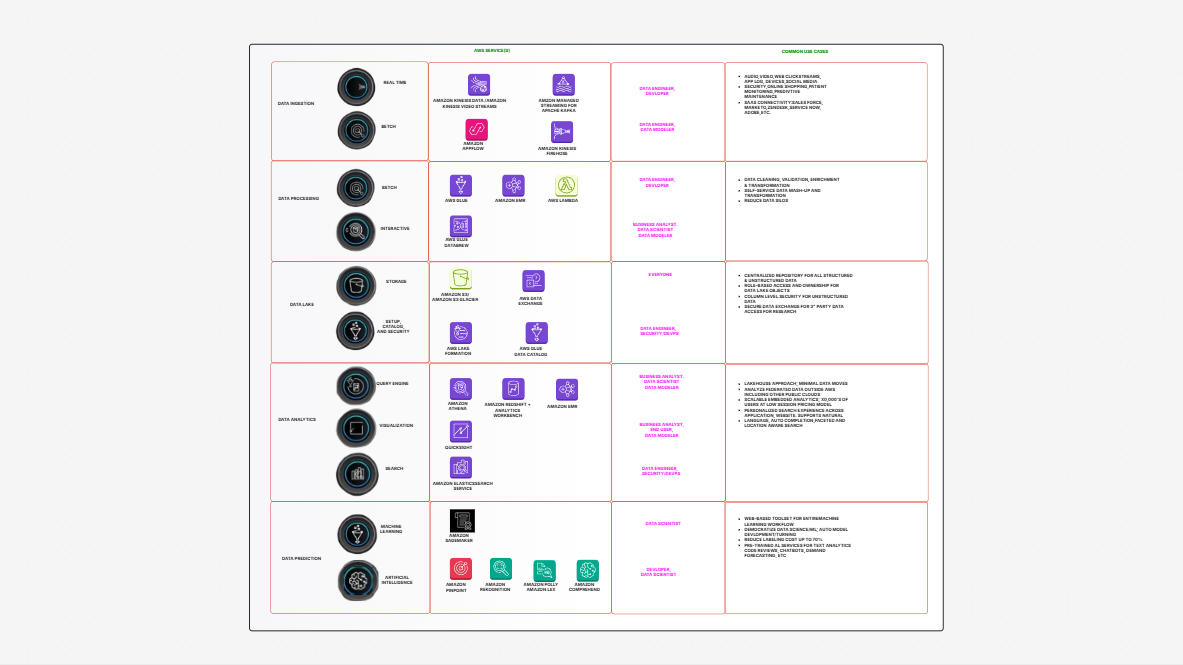
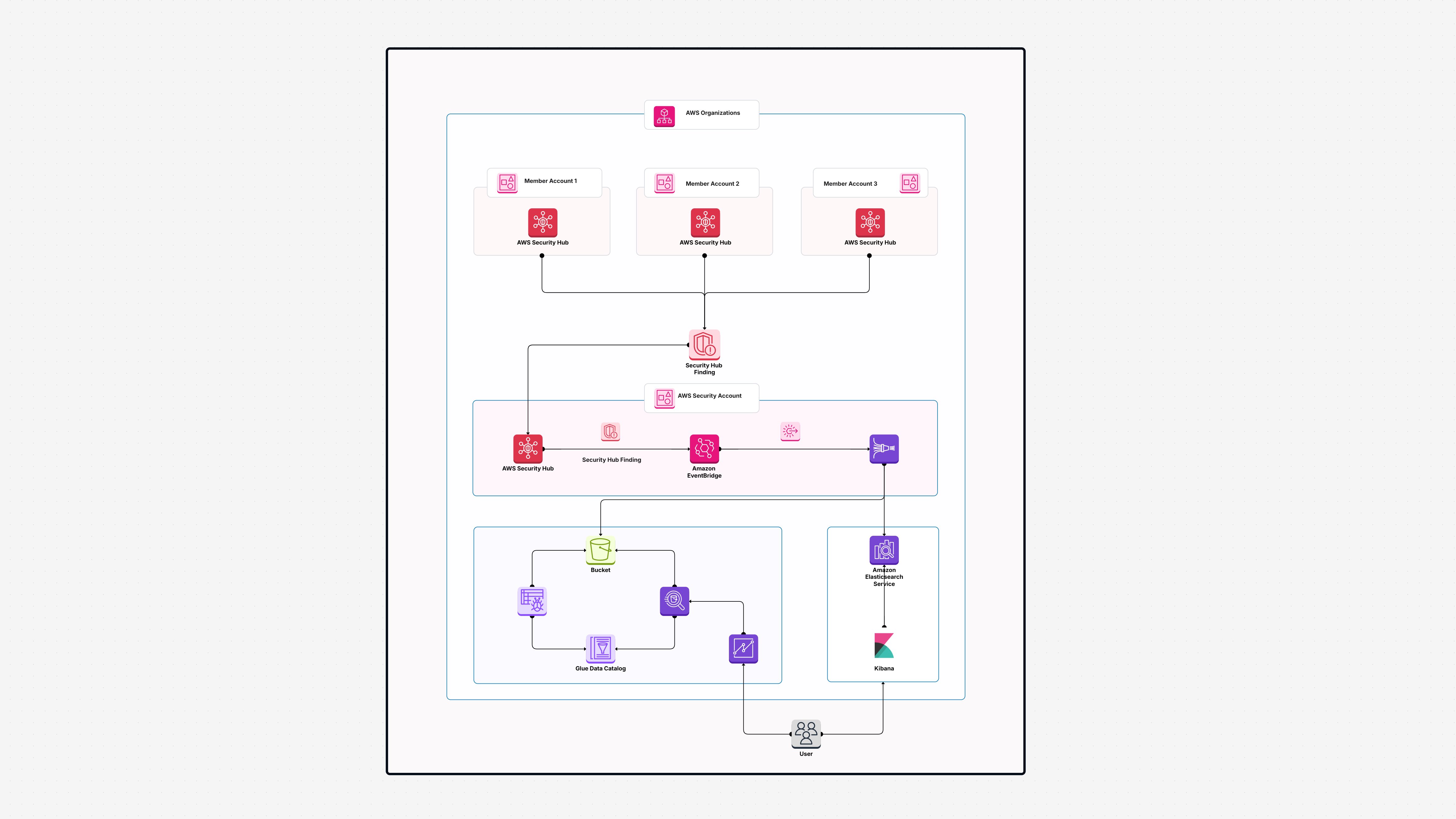
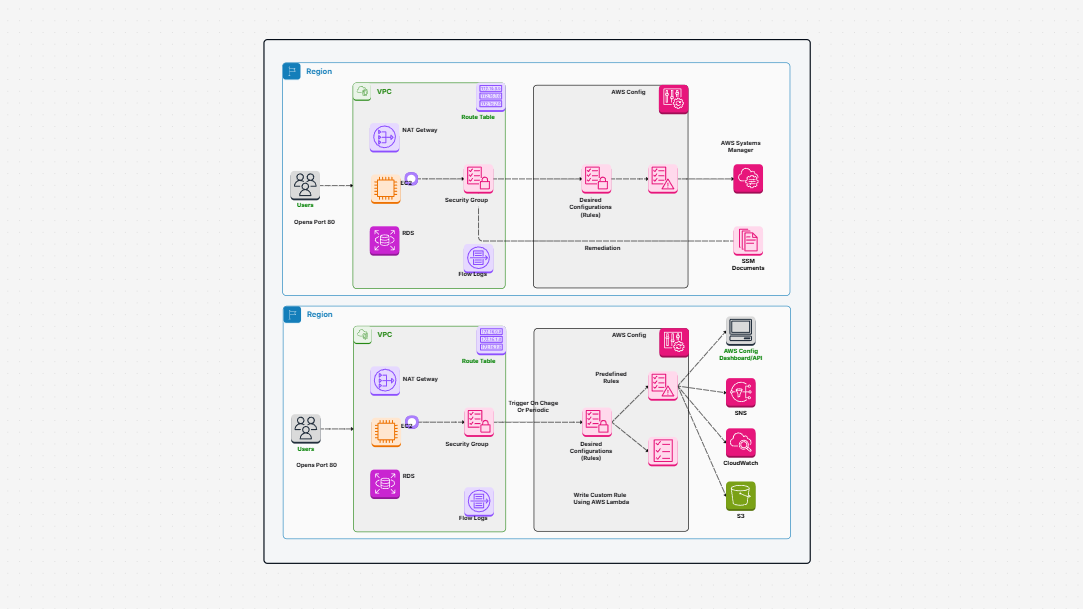
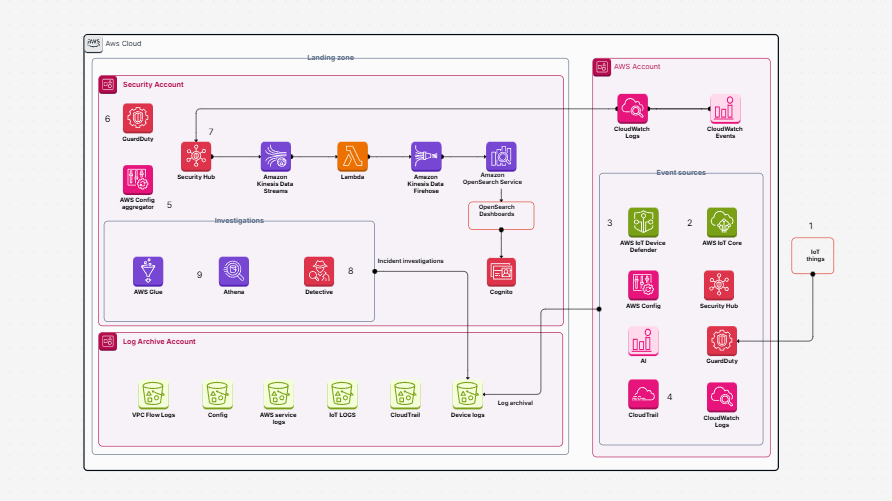
AWS Architecture Diagram
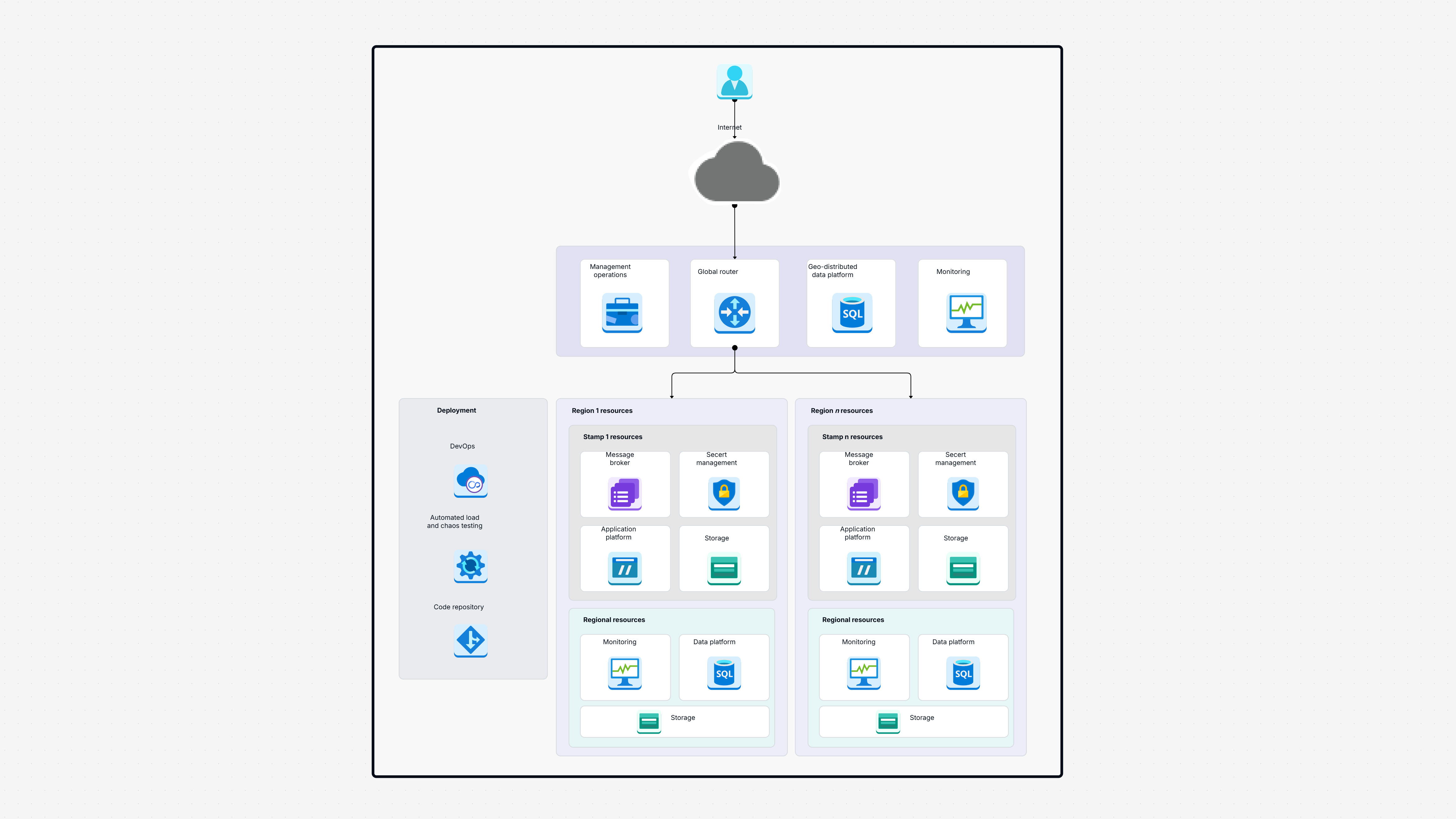
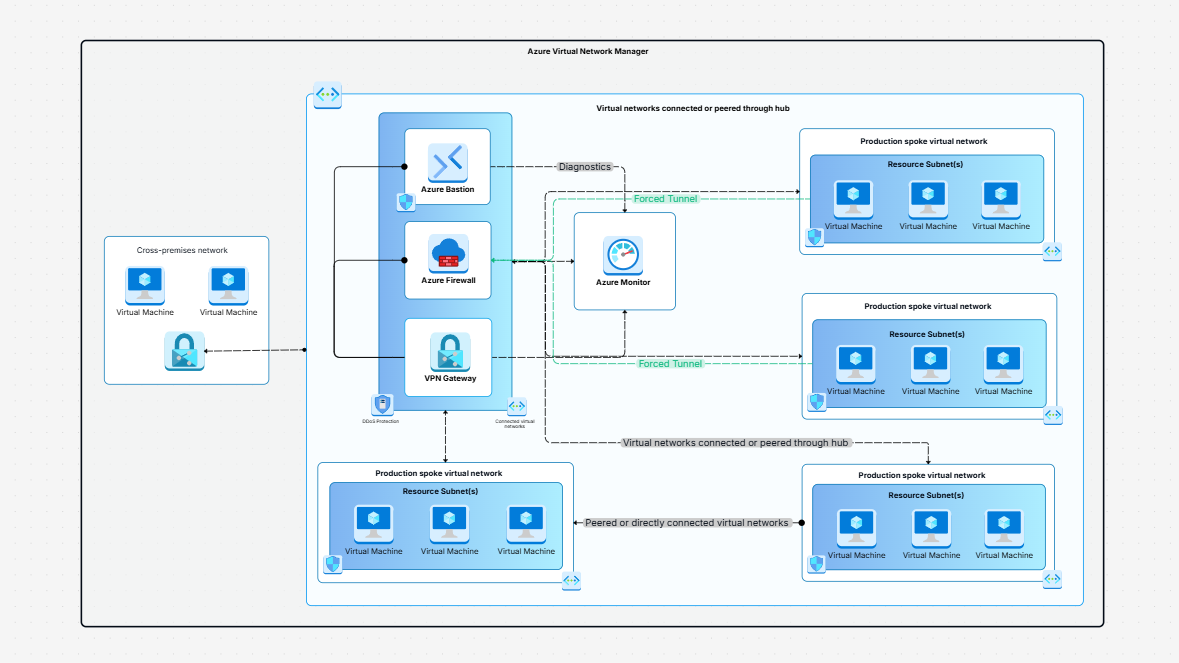
Azure Architecture Diagram
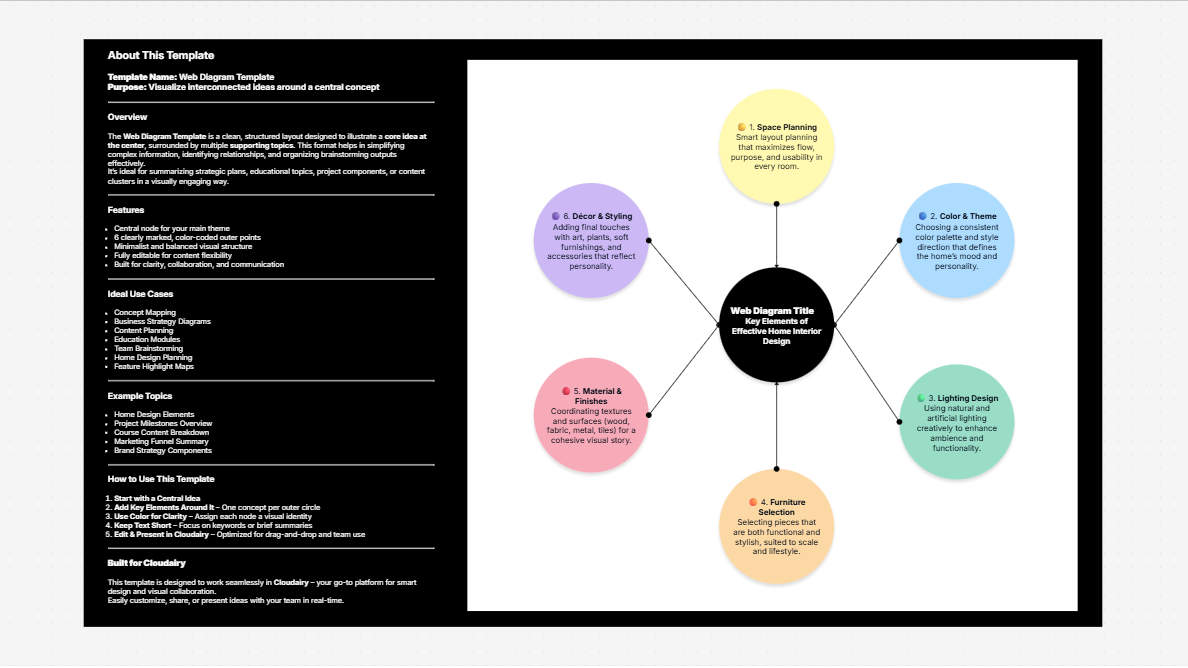
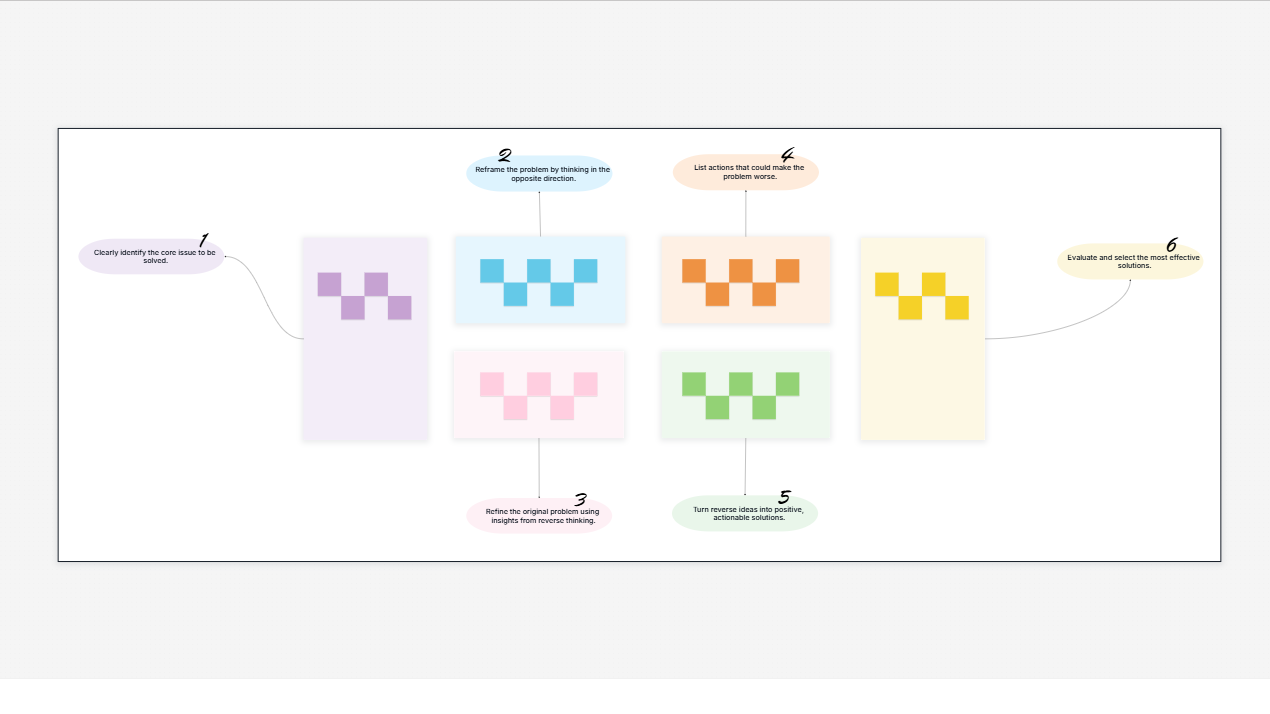
Brainstorming
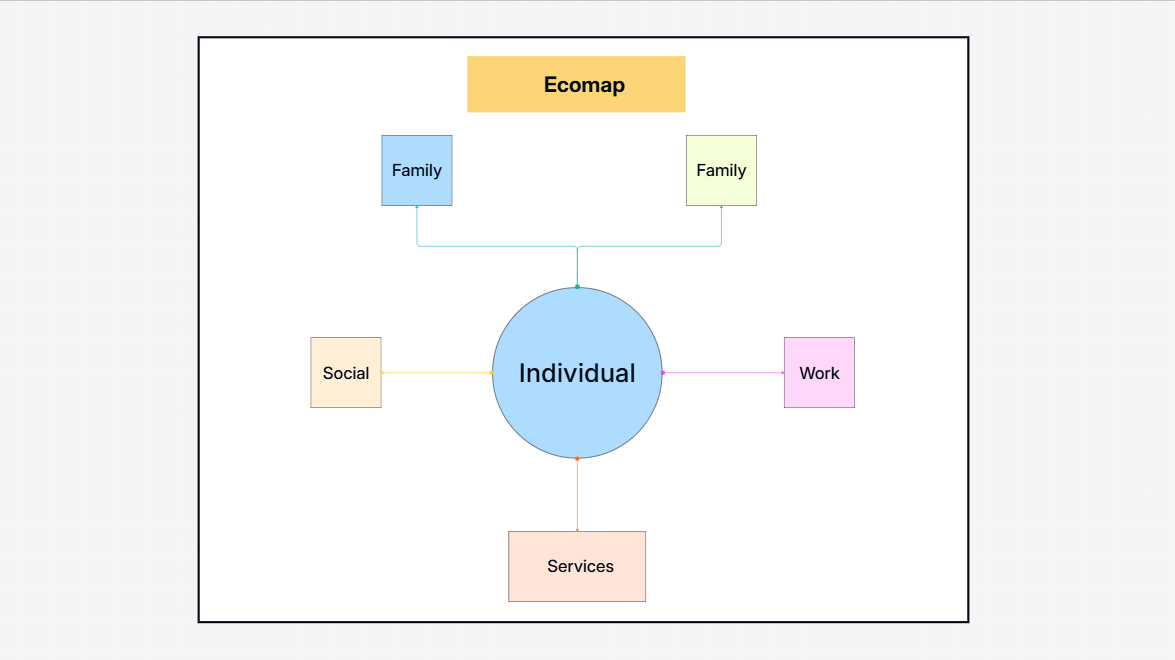
Diagramming
Documentation
Education
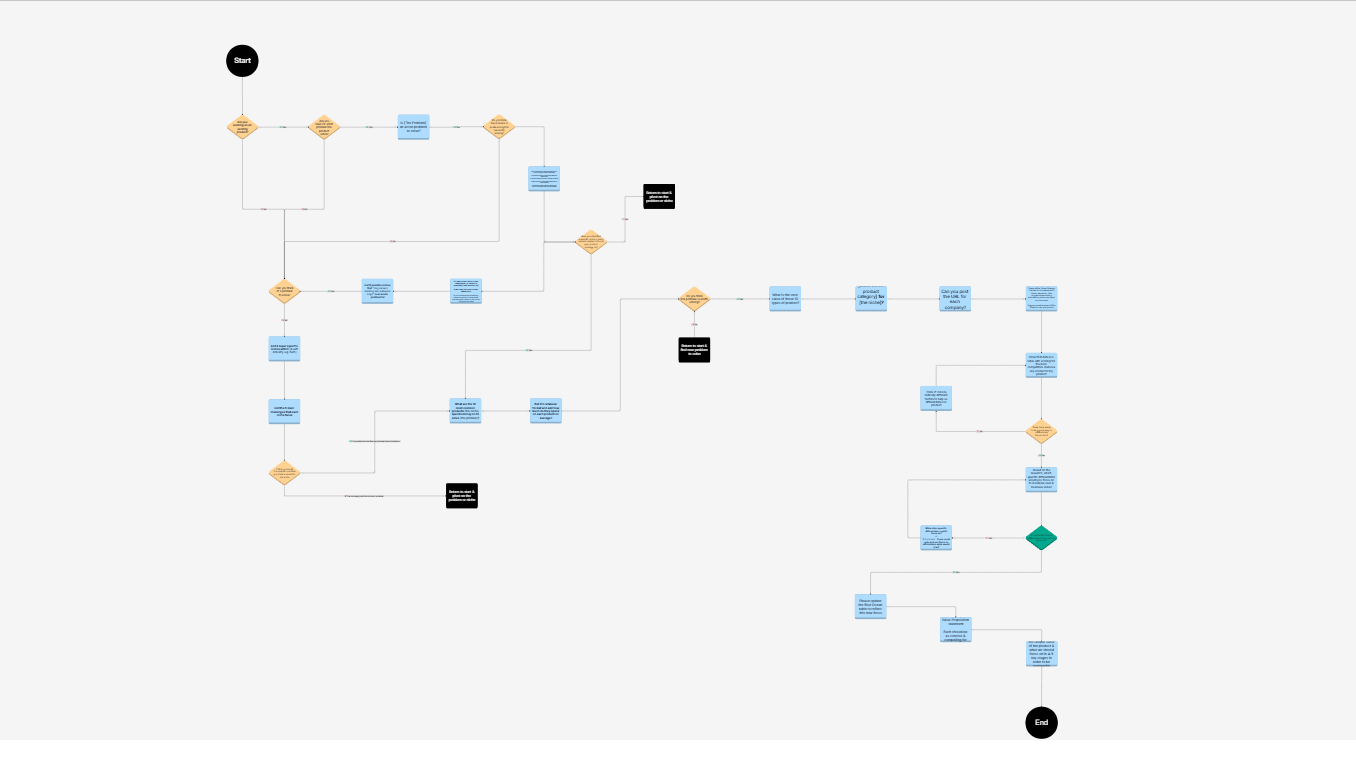
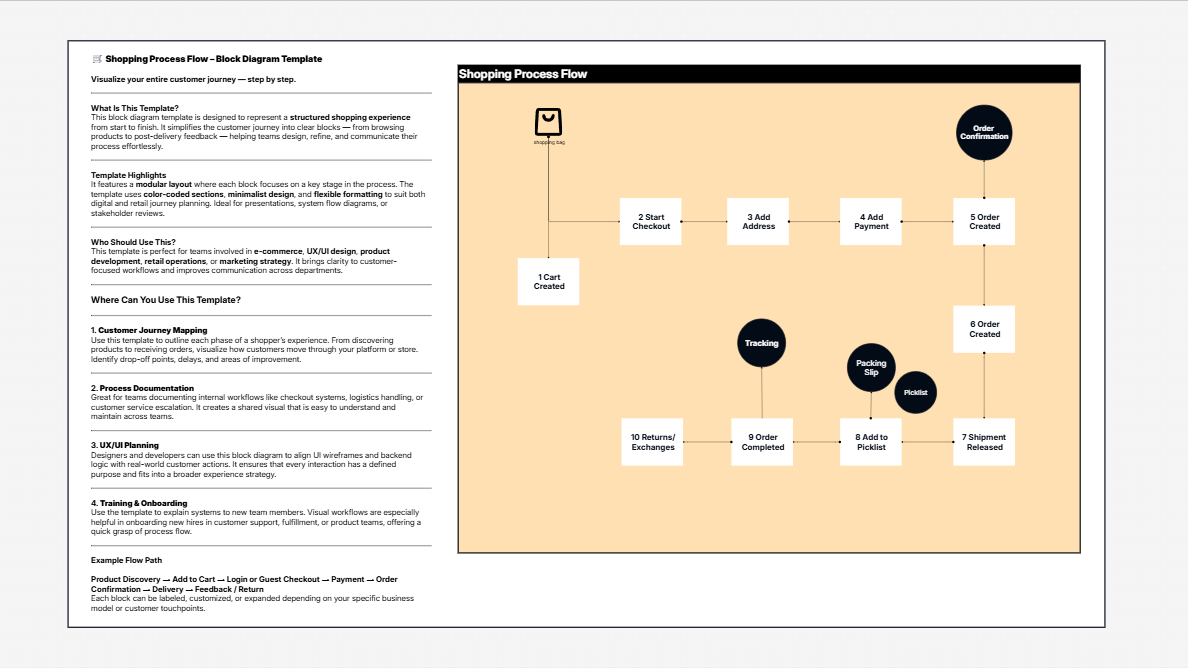
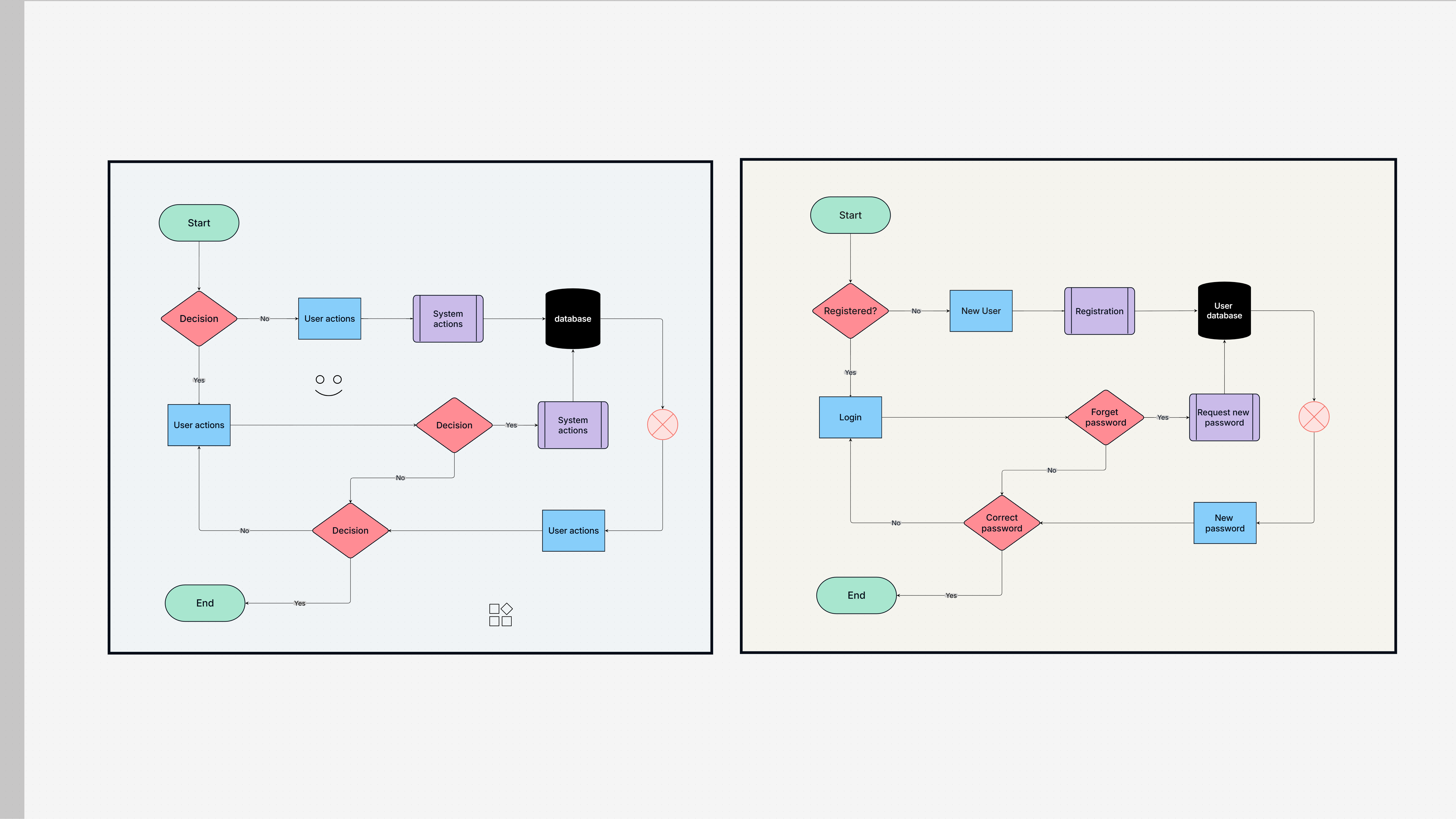
Flowchart
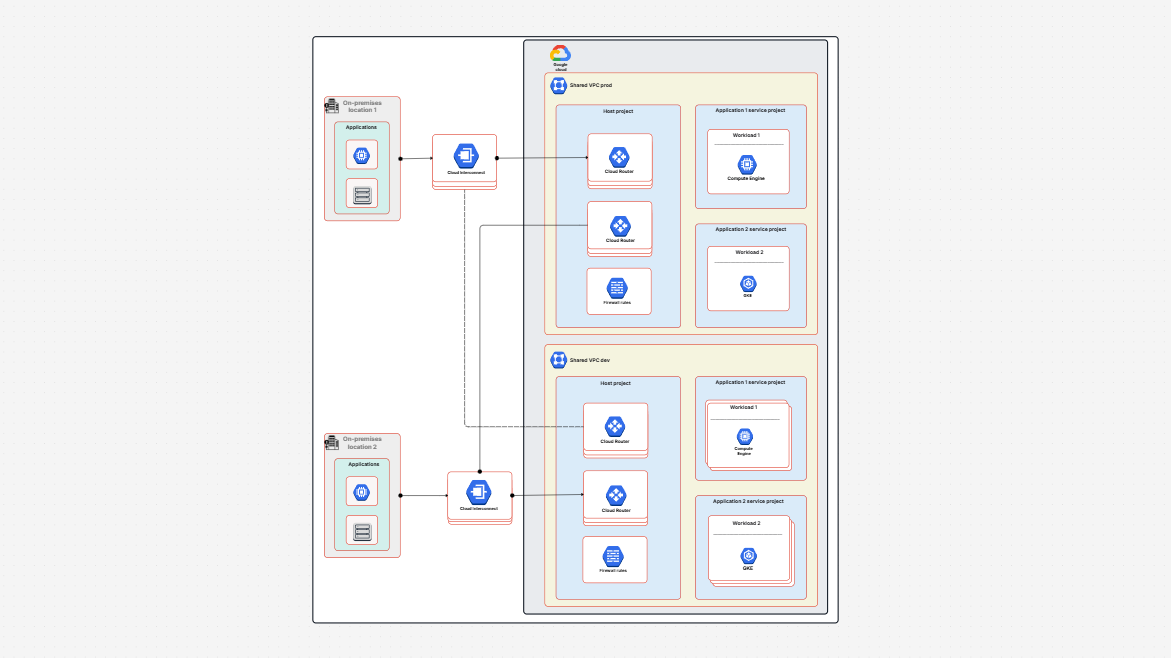
GCP Architecture Diagram
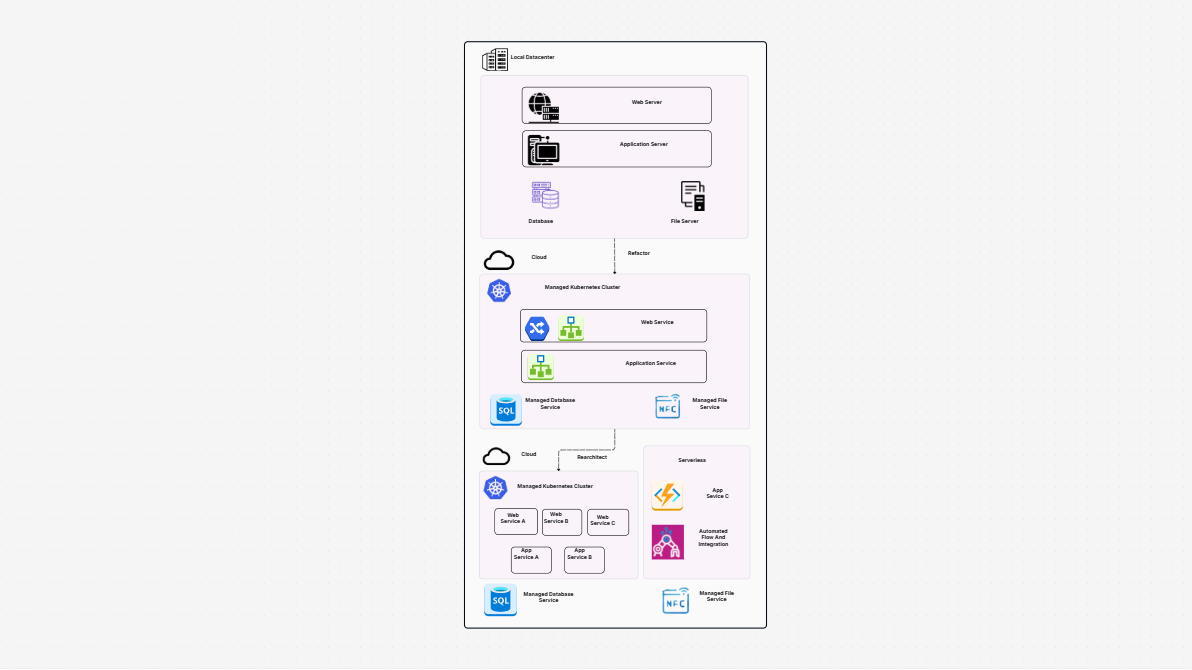
Hybrid Infrastructure
Knowledge Base
Meeting
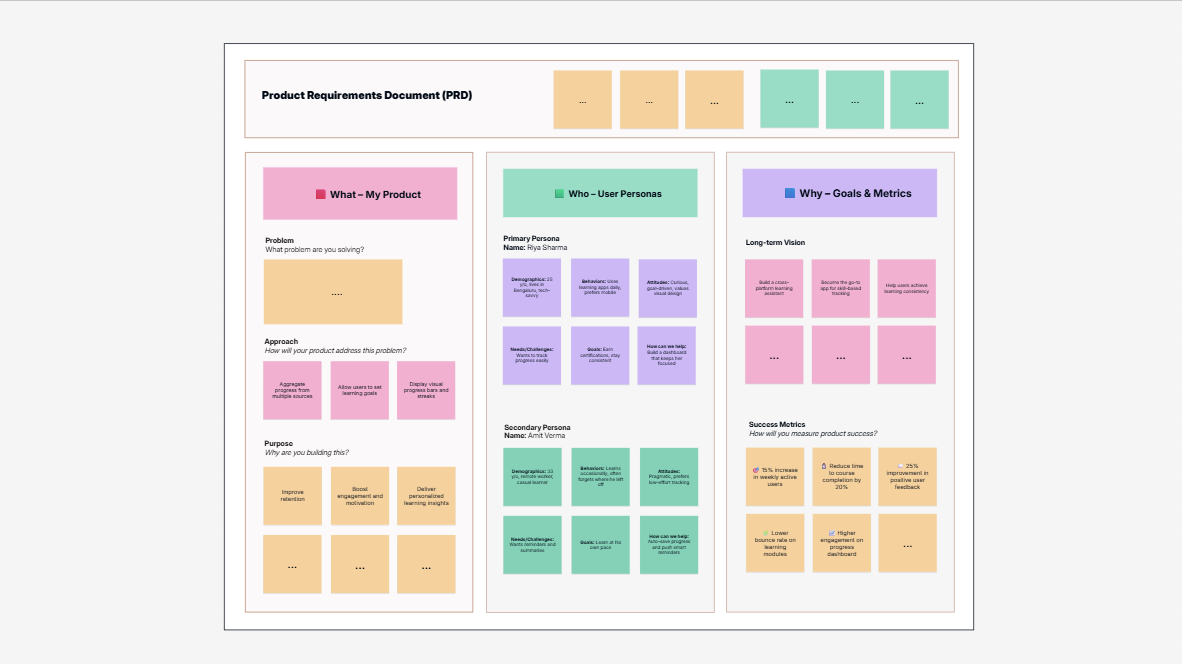
Project Doc
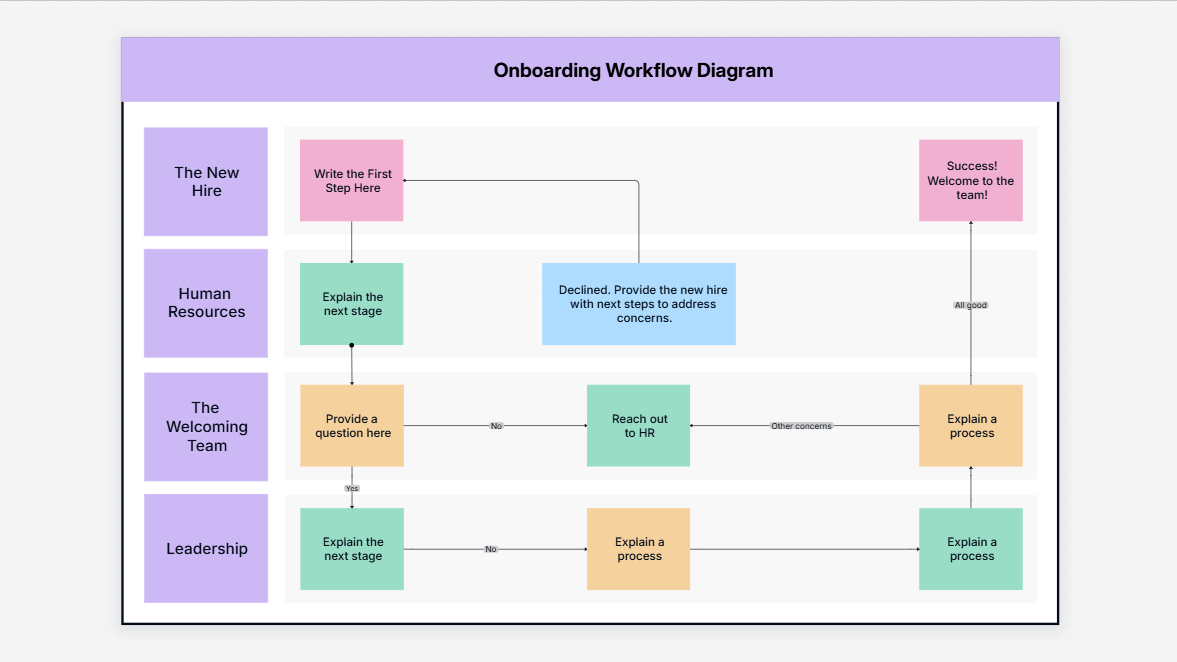
Project Management
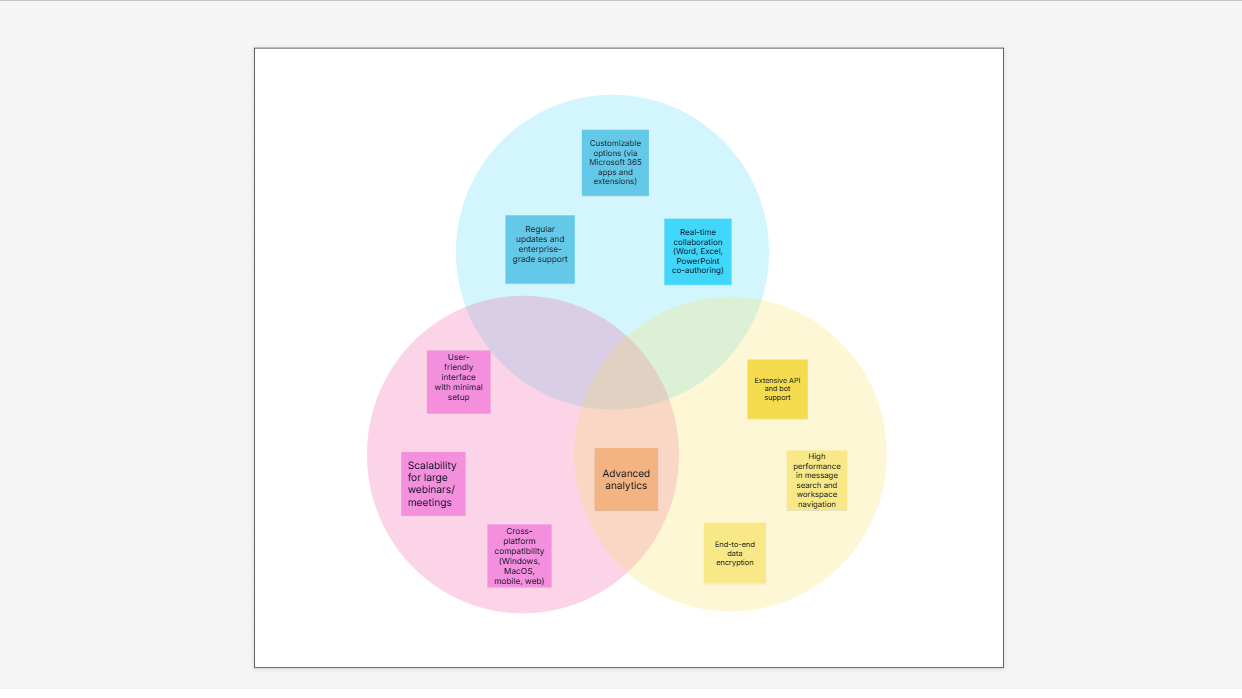
Research & Design
Retrospective
Roadmap
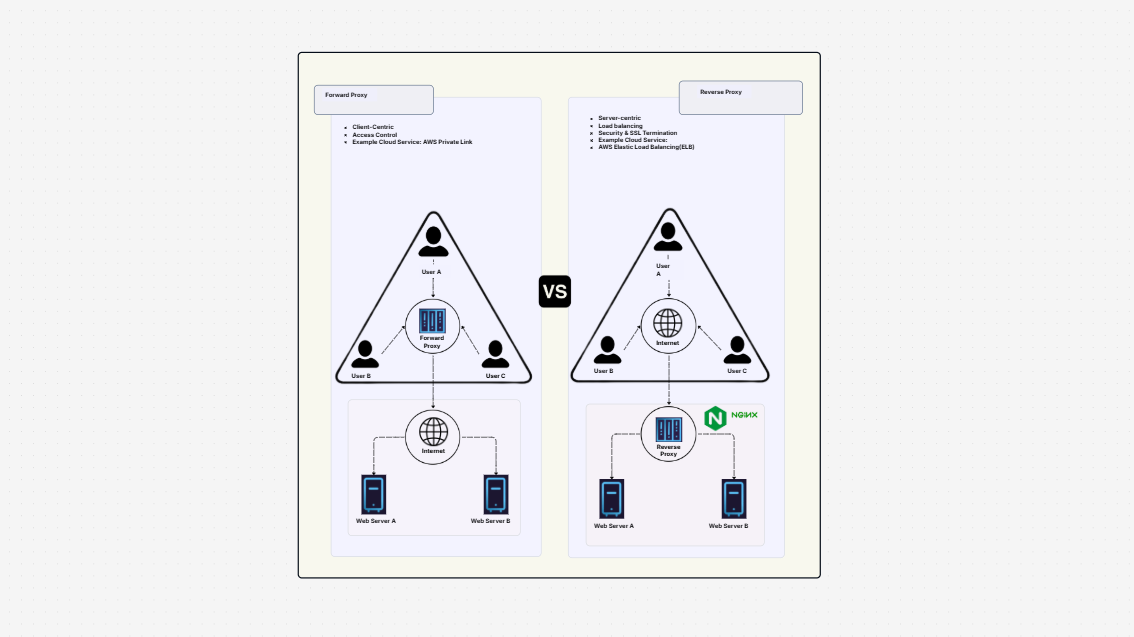
Security Architecture
Strategy & Planning
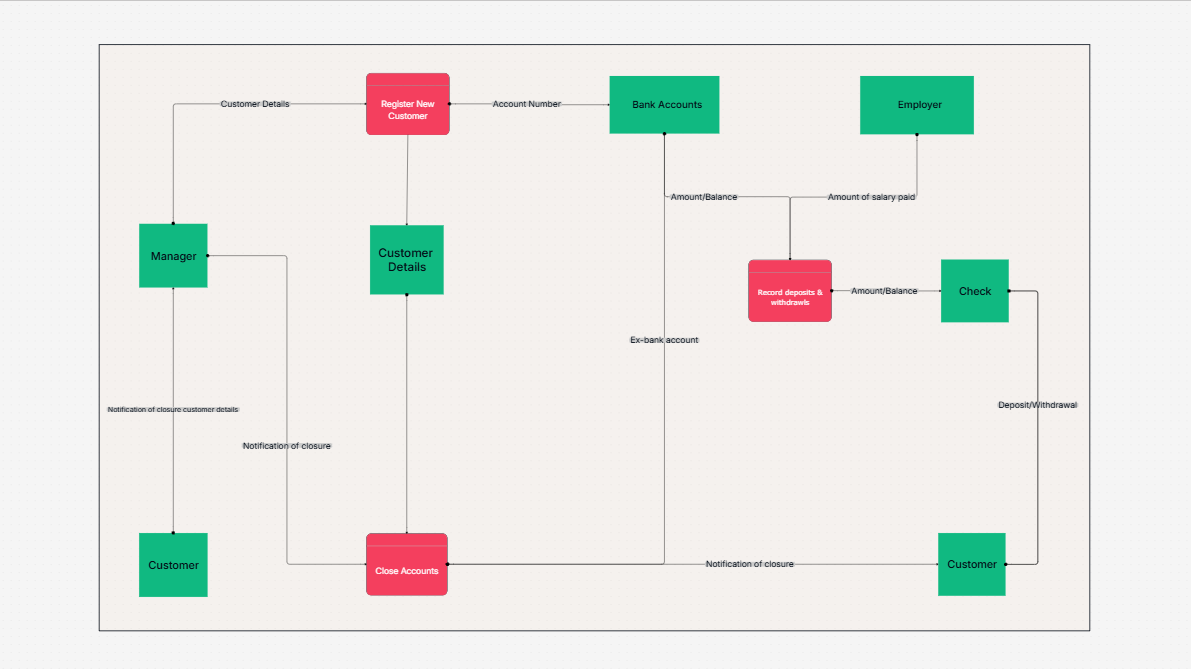
System Design
Technical Specs
UML diagram
Workflow
Workshop
Design, collaborate, innovate with Cloudairy
Unlock AI-driven design and teamwork. Start your free trial today










Design, collaborate, innovate with Cloudairy
Unlock AI-driven design and teamwork. Start your free trial today