Designing Network Security Architectures

Get your team started in minutes
Sign up with your work email for seamless collaboration.

Network security architecture is the blueprint that governs how traffic moves, where trust is established, and how threats are contained. Rather than depending on a single perimeter, it layers controls—segmentation, gateway inspection, encrypted paths, and continuous monitoring—close to applications and data. The goal is simple: reduce blast radius, make attacker movement difficult, and gather evidence. Done right, it aligns with zero trust, hybrid cloud realities, and the way modern teams actually work.
Hybrid work, SaaS growth, and multi-cloud have dissolved traditional boundaries, yet attackers still rely on lateral movement and identity abuse. A modern network security architecture addresses both by shrinking trust zones, validating context on every hop, and logging with intent. It supports app-level access (ZTNA) alongside selective inspection, reducing performance tradeoffs. Most importantly, it makes security observable and repeatable so leaders can prove outcomes: fewer pathways, faster revocation, and cleaner audits.
Great designs feel simple to use but strict under the hood. First, segment by value so critical data and workloads live behind tighter, purpose-built paths. Second, minimize implicit trust by replacing broad access with contextual, app-level authorization that can change mid-session. Third, design for observability so every decision and packet of interest is attributable and reviewable. These principles translate into tangible wins: reduced blast radius, predictable performance, and evidence on demand.
Segmentation is more than VLANs it’s a deliberate map of who talks to what, why, and how much. Group systems by business function and data sensitivity, then erect policy-aware boundaries between them. Use microsegmentation to tame east–west traffic in data centers and clouds. Couple segments with named, audited paths so “unknown flows” are easy to spot and block. The outcome is smaller failure domains and fewer default highways for attackers to traverse.
Implicit trust is where breaches grow. Replace “inside equals trusted” with contextual access decisions that consider identity, device posture, and behavior. Prefer application-level access (ZTNA) to blanket VPNs, and require step-up MFA for sensitive actions. Keep tokens short-lived and bind them to devices where possible. With continuous evaluation, access can tighten when risk rises—without tearing down every session. Users stay productive while your control plane stays decisive.
If you can’t observe it, you can’t defend it. Instrument gateways, meshes, and endpoints to emit structured logs and traces. Send them to SIEM/XDR where analytics correlate anomalies with identity and segment context. Pre-plan response actions—quarantine, re-auth, or route cuts—so automation can act within seconds. When incidents happen, rich telemetry turns confusion into evidence: who accessed what, from where, with which assurance, and how it deviated from normal.
Explore Cloudinary Network Security Architecture Templates for secure media delivery.
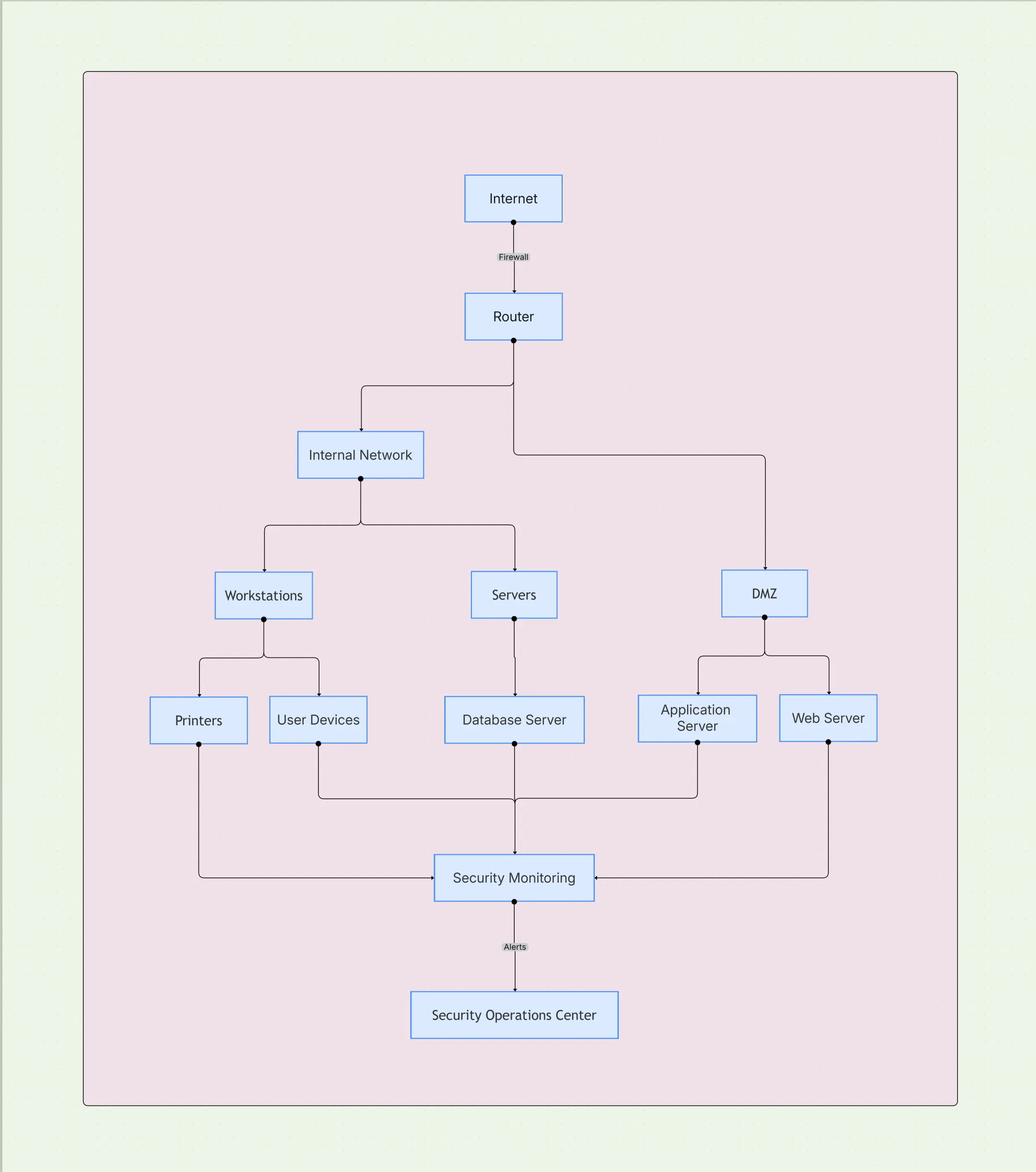
Intro: A practical diagram clarifies where policies execute and where telemetries converge. Begin at the “front doors,” trace traffic through segments, and end at monitoring and response. The numbered components below map directly to the Network Security Architecture Diagram Template and align with Zero Trust and IAM so identity and network decisions reinforce each other.
Intro: Ship value in small, auditable slices. Pick a protection surface, segment it, enforce app-level access, and prove better outcomes. Then iterate outward. The steps below align with the Security Architecture Diagram Tool and reuse patterns from Zero Trust and Monitoring so designs stay coherent and measurable.
Intro: Most network programs stumble by copying old perimeter habits into modern environments. Others over-inspect everything and crush performance, or they segment without observability. Use these pitfalls as a quarterly checklist. Each one pairs a symptom with a corrective action that improves both security and usability so progress is visible to engineers, auditors, and leadership alike.
Designing network security architectures is about clarity: clear paths, clear policies, and clear evidence. Segment by value, replace broad trust with contextual access, and centralize telemetry so response is fast and defensible. Start with one protection surface, prove better outcomes, and scale the pattern. Build your diagram with the Network Security Architecture Template in the Security Architecture Diagram Tool, and interlink with Zero Trust, IAM, and Security Monitoring for end-to-end assurance. Explore robust protection strategies for Application Security on AWS.
1.How does network security architecture relate to Zero Trust?
2.Do I need microsegmentation everywhere?
3.Is ZTNA a VPN replacement?
4.How do I prove improvements to leadership?
5.How do cloud and on-prem fit together?
Start using Cloudairy to design diagrams, documents, and workflows instantly. Harness AI to brainstorm, plan, and build—all in one platform.
.webp)
.webp)
.webp)