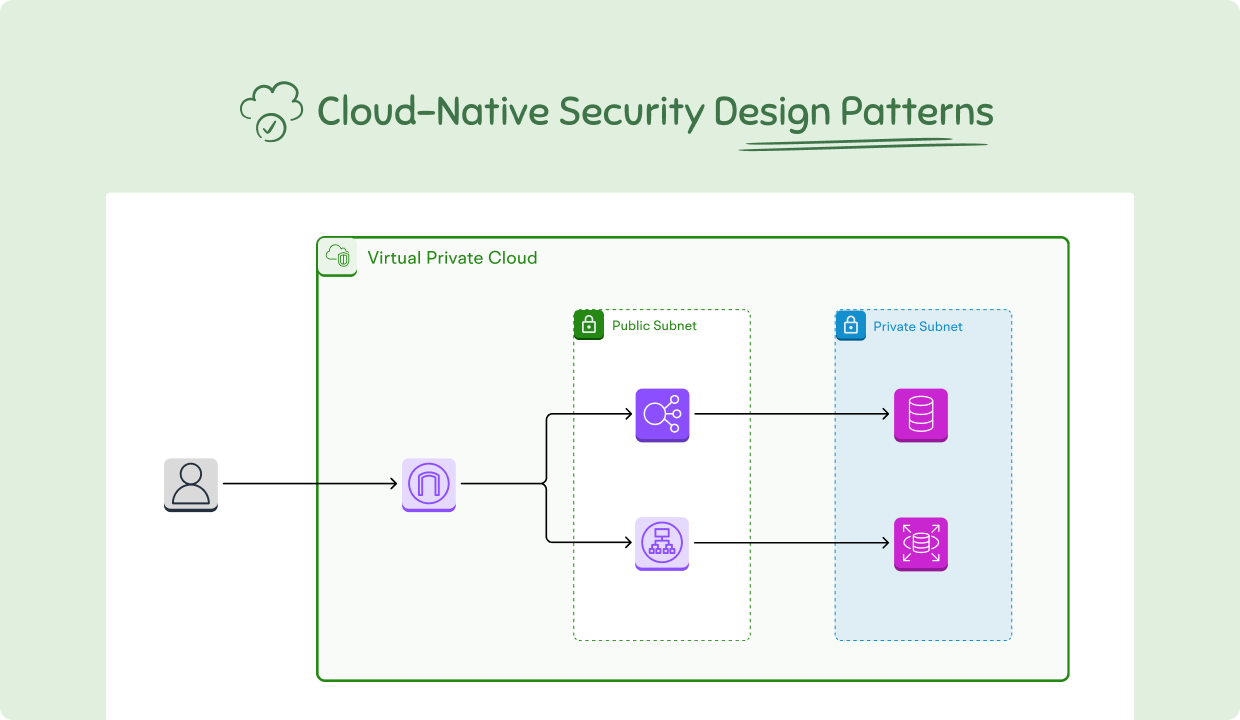
Cloud-Native Security Design Patterns

Get your team started in minutes
Sign up with your work email for seamless collaboration.

Cloud-native security design patterns are repeatable solutions that harden containers, microservices, and serverless workloads by default. They pair identity-aware access with declarative controls, so environments remain consistent from build to runtime. Instead of perimeter rules and manual gates, these patterns use automation, short-lived credentials, and continuous verification. The payoff is cleaner deployments, faster incident response, and measurable risk reduction across multi-cloud and hybrid estates—without slowing down product teams.
Model patterns visually with the Cloud Security Architecture Diagram inside the Security Architecture Diagram Tool. Deep-link to Security in Microservices, Application Security, Zero Trust, IAM, and Security Monitoring.
Modern stacks ship daily, span containers, and mix managed cloud services with custom code. Attackers target CI/CD, misconfigurations, and machine identities, not just open ports. Cloud-native security design patterns move controls closer to workloads and codify them in pipelines, meshes, and gateways. By treating infrastructure as code and identity as the new perimeter, teams prevent drift, cut standing privilege, and gain evidence for audits—while keeping developer experience fast and predictable.
Cloud-native security works when security is part of how things are built, not bolted on later. Make infrastructure immutable and declarative so every change is tracked, reviewed, and reproducible. Shift left with policy-as-code, testing configs, images, and permissions as early as unit tests. Finally, bring Zero Trust to services and APIs: every call is authenticated, authorized, encrypted, and observable. These principles ensure your controls scale with releases, not against them.
Bake configurations into images and templates, then promote them through environments without manual tweaks. Version everything—network policies, IAM bindings, PodSecurity, and runtime profiles—so rollbacks are safe and auditable. Declarative drift detection keeps prod faithful to code, while golden images plus signed artifacts eliminate “it works on my machine.” The result is fewer surprises in production and faster, cleaner remediation when vulnerabilities surface.
Move security checks into CI so issues fail fast and cheaply. Scan Dockerfiles, IaC, SBOMs, and permissions before merge; block builds when risky patterns appear. Express guardrails as code (OPA/Rego, Sentinel, Kyverno), reviewed like any PR. Because policies live beside application code, teams see rules in context, understand exceptions, and contribute improvements—turning governance into a shared, lightweight practice.
Treat every service call as untrusted until proven otherwise. Use a mesh or identity-aware proxies to enforce mTLS, validate JWTs, and apply ABAC/RBAC consistently. Keep tokens short-lived and bind them to workload identity, not shared secrets. Authorize per-method and per-dataset; log decisions with request identity and device/workload posture so investigations are fast, precise, and defensible.
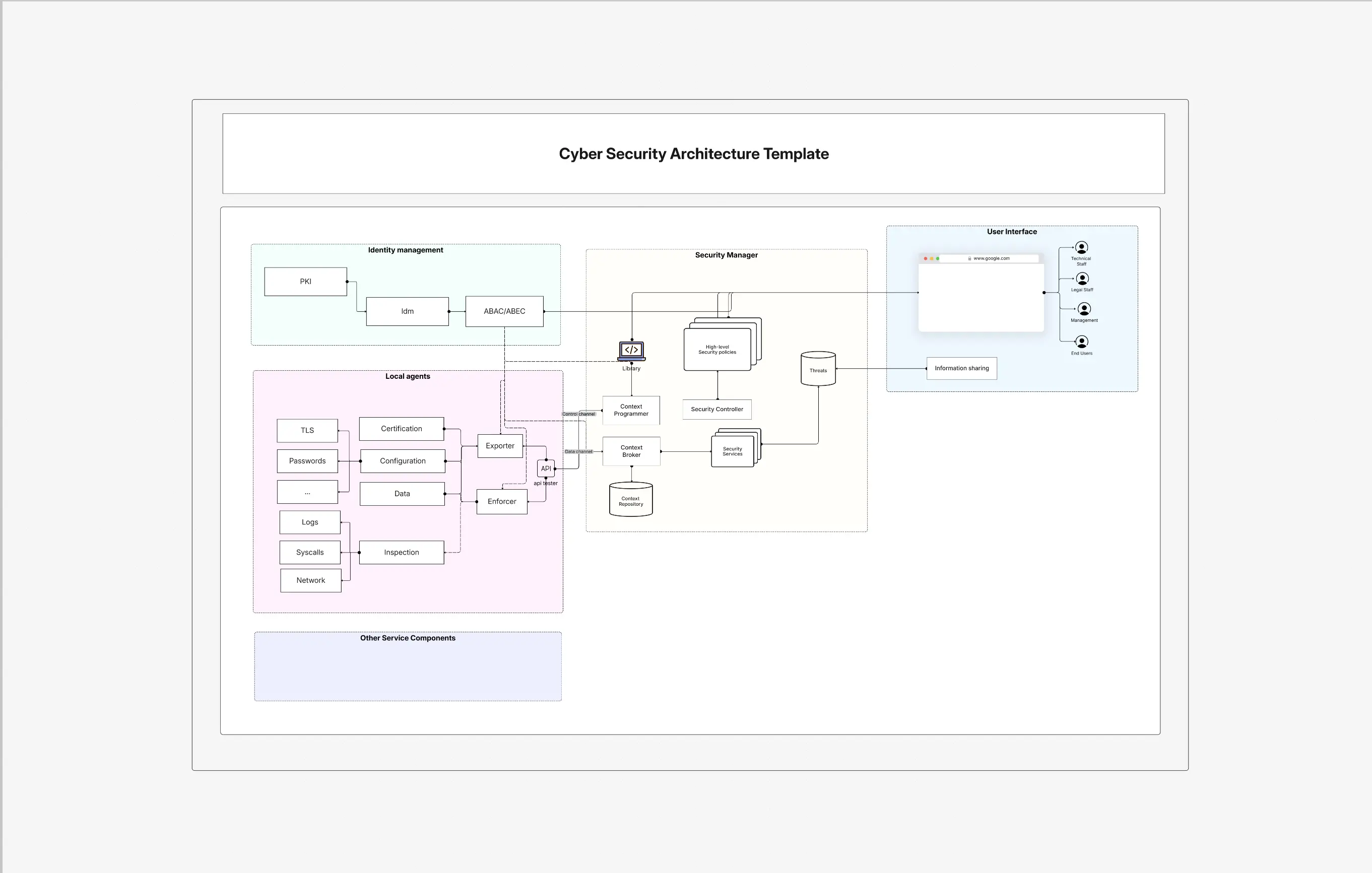
The patterns below are vendor-neutral and battle-tested across containers, Kubernetes, and serverless. They’re designed to knit together: identity-aware ingress narrows exposure, the mesh secures east-west, workload identity removes secrets, and policy-as-code keeps everything honest. Use the numbering as a checklist and map each item onto your diagram for shared understanding across app, platform, and security teams.
Your diagram should tell one story: identity at the front door, mTLS inside, data protected everywhere, and telemetry stitched together. The numbered composition below maps to layers you can drag into the Cloud Security Architecture Diagram so platform, app, and security teams share a living, auditable model.
Ship in thin, end-to-end slices. Prove a pattern on one service path, then scale horizontally. Each step below has a measurable outcome—reduced standing privilege, fewer reachable paths, or faster rollback—so progress stays visible to leadership and auditors.
Most setbacks come from copying perimeter habits into dynamic platforms or leaving secrets and policies out of CI. Treat the pitfalls below as a quarterly hygiene list; each fix strengthens both resilience and developer experience.
Cloud-native security succeeds when patterns are codified, identity-aware, and observable. Start at ingress with token-validated access, secure east-west with MTLS and policy, remove secrets via workload identity, and wire telemetry to automated response. Build your living diagram with the Cloud Security Architecture Diagram in the Security Architecture Diagram Tool, and interlink with Microservices, Application Security, Zero Trust, IAM, and Security Monitoring for end-to-end assurance.
1. How do cloud-native security patterns differ from traditional controls?
2. Do I need a service mesh to do Zero Trust?
3. How do I remove hardcoded secrets safely?
4. What’s the fastest first win?
5. How do I prove improvement?
Start using Cloudairy to design diagrams, documents, and workflows instantly. Harness AI to brainstorm, plan, and build—all in one platform.
.webp)
.webp)